中小型企业网网络搭建ensp模拟
·
所有配置全部公开,不要盲目复制,配置仅供参考和教学意义,做不通好好检查内容,不要赖我实验有问题,讲解视频及完整实验打包,私信寻米 !
2024-12-23-12:33 实验第三次校验,并完成录制讲解视频,稳定过

--------------------------------------------------------------------------------------------------------------------------------
正题开始

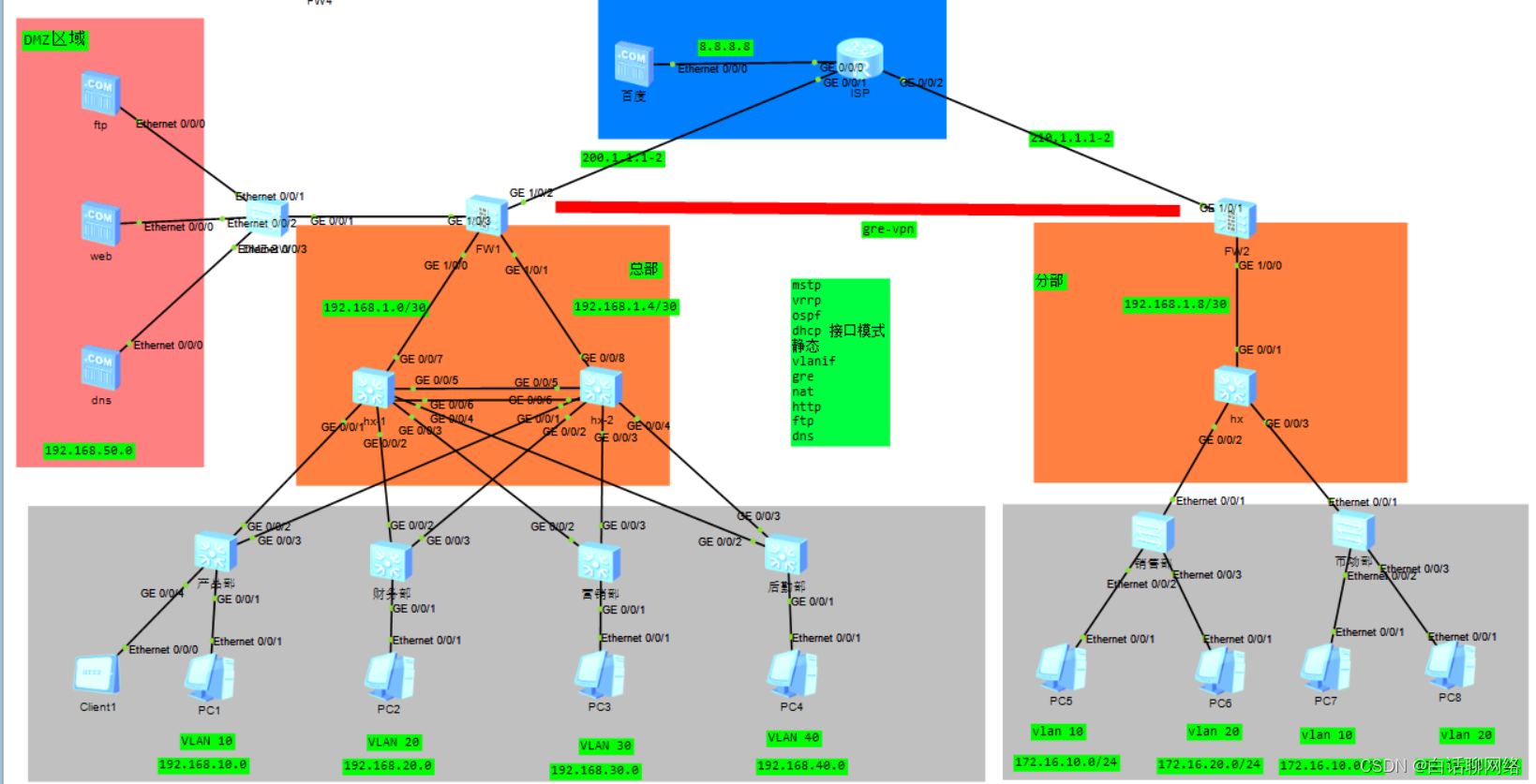
本期模拟中小型企业的万能组网,该场景为总部与分部之间的跨运营商互访,如果拆开来,就是小型企业的内网环境,技术可以任意搭配
拆开场景1:总部部署STP\RSTP\VRRP\OSPF\静态,基于防火墙的GRE VPN\IPSEC VPN、NAT
拆开场景2:总部部署STP\MSTP\VRRP负载\OSPF\静态,基于防火墙的GRE VPN\IPSEC VPN、NAT
拆开场景3:只有总部,没有分部,部署STP\MSTP\VRRP负载\OSPF\静态,基于防火墙的NAT
本期模拟的是场景2,选配GRE隧道方式实现总部与分部之间访问,灰色区域为接入层设备,橘色为核心层设备,直接上配置
总部接入层配置
sysname sw1
#
vlan batch 10
#
stp region-configuration
region-name huawei
instance 1 vlan 10 20
instance 2 vlan 30 40
active region-configuration
#
interface GigabitEthernet0/0/1
port link-type access
port default vlan 10
#
interface GigabitEthernet0/0/2
port link-type trunk
port trunk allow-pass vlan 10
#
interface GigabitEthernet0/0/3
port link-type trunk
port trunk allow-pass vlan 10
#
interface GigabitEthernet0/0/4
port link-type access
port default vlan 10
总部核心交换机1
sysname HX-1
#
vlan batch 10 20 30 40 100
#
stp instance 1 root primary
stp instance 2 root secondary
#
dhcp enable
#
stp region-configuration
region-name huawei
instance 1 vlan 10 20
instance 2 vlan 30 40
active region-configuration
#
ip pool vlan10
gateway-list 192.168.10.254
network 192.168.10.0 mask 255.255.255.0
dns-list 192.168.50.3
#
ip pool vlan20
gateway-list 192.168.20.254
network 192.168.20.0 mask 255.255.255.0
dns-list 192.168.50.3
#
ip pool vlan30
gateway-list 192.168.30.254
network 192.168.30.0 mask 255.255.255.0
dns-list 192.168.50.3
#
ip pool vlan40
gateway-list 192.168.40.254
network 192.168.40.0 mask 255.255.255.0
dns-list 192.168.50.3
#
interface Vlanif10
ip address 192.168.10.252 255.255.255.0
vrrp vrid 10 virtual-ip 192.168.10.254
vrrp vrid 10 priority 120
vrrp vrid 10 track interface GigabitEthernet0/0/7 reduced 30
dhcp select global
#
interface Vlanif20
ip address 192.168.20.252 255.255.255.0
vrrp vrid 20 virtual-ip 192.168.20.254
vrrp vrid 20 priority 120
vrrp vrid 20 track interface GigabitEthernet0/0/7 reduced 30
dhcp select global
#
interface Vlanif30
ip address 192.168.30.252 255.255.255.0
vrrp vrid 30 virtual-ip 192.168.30.254
dhcp select global
#
interface Vlanif40
ip address 192.168.40.252 255.255.255.0
vrrp vrid 40 virtual-ip 192.168.40.254
dhcp select global
#
interface Vlanif100
ip address 192.168.1.1 255.255.255.252
#
interface Eth-Trunk1
port link-type trunk
port trunk allow-pass vlan 10 20 30 40
#
interface GigabitEthernet0/0/1
port link-type trunk
port trunk allow-pass vlan 10
#
interface GigabitEthernet0/0/2
port link-type trunk
port trunk allow-pass vlan 20
#
interface GigabitEthernet0/0/3
port link-type trunk
port trunk allow-pass vlan 30
#
interface GigabitEthernet0/0/4
port link-type trunk
port trunk allow-pass vlan 40
#
interface GigabitEthernet0/0/5
eth-trunk 1
#
interface GigabitEthernet0/0/6
eth-trunk 1
#
interface GigabitEthernet0/0/7
port link-type access
port default vlan 100
#
ospf 1
area 0.0.0.0
network 192.168.1.1 0.0.0.0
area 0.0.0.1
network 192.168.10.0 0.0.0.255
network 192.168.20.0 0.0.0.255
network 192.168.30.0 0.0.0.255
network 192.168.40.0 0.0.0.255
总部核心交换机2
sysname HX-2
#
vlan batch 10 20 30 40 100
#
stp instance 1 root secondary
stp instance 2 root primary
#
dhcp enable
#
stp region-configuration
region-name huawei
instance 1 vlan 10 20
instance 2 vlan 30 40
active region-configuration
#
ip pool vlan10
gateway-list 192.168.10.254
network 192.168.10.0 mask 255.255.255.0
dns-list 192.168.50.3
#
ip pool vlan20
gateway-list 192.168.20.254
network 192.168.20.0 mask 255.255.255.0
dns-list 192.168.50.3
#
ip pool vlan30
gateway-list 192.168.30.254
network 192.168.30.0 mask 255.255.255.0
dns-list 192.168.50.3
#
ip pool vlan40
gateway-list 192.168.40.254
network 192.168.40.0 mask 255.255.255.0
dns-list 192.168.50.3
#
interface Vlanif10
ip address 192.168.10.253 255.255.255.0
vrrp vrid 10 virtual-ip 192.168.10.254
dhcp select global
#
interface Vlanif20
ip address 192.168.20.253 255.255.255.0
vrrp vrid 20 virtual-ip 192.168.20.254
dhcp select global
#
interface Vlanif30
ip address 192.168.30.253 255.255.255.0
vrrp vrid 30 virtual-ip 192.168.30.254
vrrp vrid 30 priority 120
vrrp vrid 30 track interface GigabitEthernet0/0/7 reduced 30
dhcp select global
#
interface Vlanif40
ip address 192.168.40.253 255.255.255.0
vrrp vrid 40 virtual-ip 192.168.40.254
vrrp vrid 40 priority 120
vrrp vrid 40 track interface GigabitEthernet0/0/7 reduced 30
dhcp select global
#
interface Vlanif100
ip address 192.168.1.5 255.255.255.252
#
interface Eth-Trunk1
port link-type trunk
port trunk allow-pass vlan 10 20 30 40
#
interface GigabitEthernet0/0/1
port link-type trunk
port trunk allow-pass vlan 10
#
interface GigabitEthernet0/0/2
port link-type trunk
port trunk allow-pass vlan 20
#
interface GigabitEthernet0/0/3
port link-type trunk
port trunk allow-pass vlan 30
#
interface GigabitEthernet0/0/4
port link-type trunk
port trunk allow-pass vlan 40
#
interface GigabitEthernet0/0/5
eth-trunk 1
#
interface GigabitEthernet0/0/6
eth-trunk 1
#
interface GigabitEthernet0/0/7
port link-type access
port default vlan 100
#
ospf 1
area 0.0.0.0
network 192.168.1.5 0.0.0.0
area 0.0.0.1
network 192.168.10.0 0.0.0.255
network 192.168.20.0 0.0.0.255
network 192.168.30.0 0.0.0.255
network 192.168.40.0 0.0.0.255
出口防火墙
sysname FW1
IP地址配置
interface GigabitEthernet1/0/0
ip address 192.168.1.2 255.255.255.252
#
interface GigabitEthernet1/0/1
ip address 192.168.1.6 255.255.255.252
#
interface GigabitEthernet1/0/2
ip address 200.1.1.1 255.255.255.252
#
interface GigabitEthernet1/0/3
ip address 192.168.50.254 255.255.255.0
GRE隧道配置
interface Tunnel0
ip address 10.1.12.1 255.255.255.0
tunnel-protocol gre
source 200.1.1.1
destination 210.1.1.2
接口划分区域
firewall zone trust
add interface GigabitEthernet1/0/0
add interface GigabitEthernet1/0/1
add interface Tunnel0
#
firewall zone untrust
add interface GigabitEthernet1/0/2
#
firewall zone dmz
add interface GigabitEthernet1/0/3
ospf路由配置
ospf 1
default-route-advertise
area 0.0.0.0
network 192.168.1.0 0.0.0.3
network 192.168.1.4 0.0.0.3
network 192.168.50.0 0.0.0.255
缺省路由和gre隧道路由
ip route-static 0.0.0.0 0.0.0.0 200.1.1.2
ip route-static 172.16.10.0 255.255.255.0 Tunnel0
ip route-static 172.16.20.0 255.255.255.0 Tunnel0
security-policy
rule name t-u //放行nat策略
source-zone trust
destination-zone untrust
source-address 192.168.10.0 mask 255.255.255.0
source-address 192.168.20.0 mask 255.255.255.0
source-address 192.168.30.0 mask 255.255.255.0
source-address 192.168.50.0 mask 255.255.255.0
action permit
rule name t-dmz //放行内网到dmz的流量
source-zone trust
destination-zone dmz
source-address 192.168.10.0 mask 255.255.255.0
source-address 192.168.20.0 mask 255.255.255.0
source-address 192.168.30.0 mask 255.255.255.0
destination-address 192.168.50.0 mask 255.255.255.0
action permit
rule name u-dmz //放行分支到总部dmz的流量
source-zone untrust
destination-zone dmz
source-address 172.16.10.0 mask 255.255.255.0
source-address 172.16.20.0 mask 255.255.255.0
destination-address 192.168.50.0 mask 255.255.255.0
action permit
rule name l-u //gre建立隧道策略
source-zone local
source-zone untrust
destination-zone local
destination-zone untrust
action permit
rule name gre //gre正向的流量
source-zone trust
destination-zone untrust
source-address 192.168.10.0 mask 255.255.255.0
source-address 192.168.20.0 mask 255.255.255.0
source-address 192.168.30.0 mask 255.255.255.0
source-address 192.168.50.0 mask 255.255.255.0
destination-address 172.16.10.0 mask 255.255.255.0
destination-address 172.16.20.0 mask 255.255.255.0
action permit
rule name gre- //gre反向的流量
source-zone untrust
destination-zone trust
source-address 172.16.10.0 mask 255.255.255.0
source-address 172.16.20.0 mask 255.255.255.0
destination-address 192.168.10.0 mask 255.255.255.0
destination-address 192.168.20.0 mask 255.255.255.0
destination-address 192.168.30.0 mask 255.255.255.0
destination-address 192.168.50.0 mask 255.255.255.0
action permit
#
nat-policy
rule name gre //nat中禁止gre的流量
source-zone trust
destination-zone untrust
source-address 192.168.10.0 mask 255.255.255.0
source-address 192.168.20.0 mask 255.255.255.0
source-address 192.168.30.0 mask 255.255.255.0
source-address 192.168.50.0 mask 255.255.255.0
destination-address 172.16.10.0 mask 255.255.255.0
destination-address 172.16.20.0 mask 255.255.255.0
action no-nat
rule name t-u //nat策略
source-zone trust
destination-zone untrust
source-address 192.168.10.0 mask 255.255.255.0
source-address 192.168.20.0 mask 255.255.255.0
source-address 192.168.30.0 mask 255.255.255.0
action source-nat easy-ip
分部接入交换机
sysname xiaoshoubu
#
vlan batch 10 20
#
interface Ethernet0/0/1
port link-type trunk
port trunk allow-pass vlan 10 20
#
interface Ethernet0/0/2
port link-type access
port default vlan 10
#
interface Ethernet0/0/3
port link-type access
port default vlan 20
分部核心交换机
sysname hx
#
vlan batch 10 20 100
#
stp instance 0 root primary
#
interface Vlanif10
ip address 172.16.10.254 255.255.255.0
#
interface Vlanif20
ip address 172.16.20.254 255.255.255.0
#
interface Vlanif100
ip address 192.168.1.9 255.255.255.252
#
interface GigabitEthernet0/0/1
port link-type access
port default vlan 100
#
interface GigabitEthernet0/0/2
port link-type trunk
port trunk allow-pass vlan 10 20
#
interface GigabitEthernet0/0/3
port link-type trunk
port trunk allow-pass vlan 10 20
#
ospf 1
area 0.0.0.0
network 192.168.1.8 0.0.0.3
network 172.16.10.0 0.0.0.255
network 172.16.20.0 0.0.0.255
分部出口防火墙
sysname FW2
#
interface GigabitEthernet1/0/0
ip address 192.168.1.10 255.255.255.252
#
interface GigabitEthernet1/0/1
ip address 210.1.1.2 255.255.255.252
#
interface Tunnel0
ip address 10.1.12.2 255.255.255.0
tunnel-protocol gre
source 210.1.1.2
destination 200.1.1.1
#
firewall zone trust
add interface GigabitEthernet1/0/0
add interface Tunnel0
#
firewall zone untrust
add interface GigabitEthernet1/0/1
#
ospf 1
default-route-advertise
area 0.0.0.0
network 192.168.1.8 0.0.0.3
#
ip route-static 0.0.0.0 0.0.0.0 210.1.1.1
ip route-static 192.168.10.0 255.255.255.0 Tunnel0
ip route-static 192.168.20.0 255.255.255.0 Tunnel0
ip route-static 192.168.30.0 255.255.255.0 Tunnel0
ip route-static 192.168.50.0 255.255.255.0 Tunnel0
#
security-policy
rule name t-u
source-zone trust
destination-zone untrust
source-address 172.16.10.0 mask 255.255.255.0
source-address 172.16.20.0 mask 255.255.255.0
action permit
rule name l-u
source-zone local
source-zone untrust
destination-zone local
destination-zone untrust
action permit
rule name gre
source-zone untrust
destination-zone trust
source-address 192.168.10.0 mask 255.255.255.0
source-address 192.168.20.0 mask 255.255.255.0
source-address 192.168.30.0 mask 255.255.255.0
source-address 192.168.50.0 mask 255.255.255.0
destination-address 172.16.10.0 mask 255.255.255.0
destination-address 172.16.20.0 mask 255.255.255.0
action permit
rule name gre-
source-zone trust
destination-zone untrust
source-address 172.16.10.0 mask 255.255.255.0
source-address 172.16.20.0 mask 255.255.255.0
destination-address 192.168.10.0 mask 255.255.255.0
destination-address 192.168.20.0 mask 255.255.255.0
destination-address 192.168.30.0 mask 255.255.255.0
destination-address 192.168.50.0 mask 255.255.255.0
action permit
#
nat-policy
rule name gre
source-zone trust
destination-zone untrust
source-address 172.16.10.0 mask 255.255.255.0
destination-address 192.168.10.0 mask 255.255.255.0
destination-address 192.168.20.0 mask 255.255.255.0
destination-address 192.168.30.0 mask 255.255.255.0
destination-address 192.168.50.0 mask 255.255.255.0
action no-nat
rule name isp
source-zone trust
destination-zone untrust
source-address 172.16.10.0 mask 255.255.255.0
source-address 172.16.20.0 mask 255.255.255.0
action source-nat easy-ip
实验测试验证
MSTP验证


Vrrp验证


Dhcp验证

Ospf验证

Nat验证


连通性测试


阅读全文
AI总结
更多推荐
 已为社区贡献4条内容
已为社区贡献4条内容
相关推荐
查看更多
鸿蒙开发工具大赶集
本仓将收集和展示鸿蒙开发工具,欢迎大家踊跃投稿。通过pr附上您的工具介绍和使用指南,并加上工具对应的链接,通过的工具将会成功上架到我们社区。
OpenManus
No fortress, purely open ground. OpenManus is Coming.
G-Star公益行
G-Star 公益行 是 GitCode G-Star 计划旗下专为公益机构打造的技术赋能计划,依托 GitCode 开源平台、生态流量、云计算与 AI 支持,旨在连接开源技术与公益组织,通过技术赋能帮助公益组织实现数字化转型,以提升运营效率、优化资源配置、拓展公益影响力。
热门开源项目
活动日历
查看更多
直播时间 2025-03-13 18:32:35


全栈自研企业级AI平台:Java核心技术×私有化部署实战
直播时间 2025-03-11 18:35:18


从0到1:Go IoT 开发平台的架构演进与生态蓝图
直播时间 2025-03-05 14:35:37


国产工作流引擎 终结「996」开发困局!
直播时间 2025-02-25 14:38:13


免费开源宝藏 ShopXO,电商系统搭建秘籍大公开!
直播时间 2025-02-18 14:31:04


从数据孤岛到数据智能 - 企业级数据管理利器深度解析
目录









所有评论(0)